
Chirag's Blog: What is RSA algorithm | RSA Algorithm explain with example | RSA algorithm example | RSA algorithm steps | how to find private key in rsa example
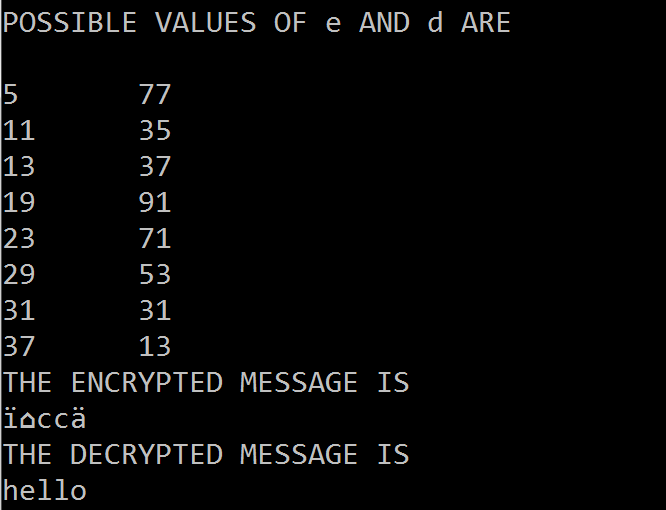
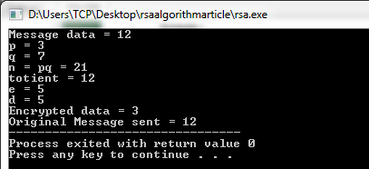
C code to implement RSA Algorithm(Encryption and Decryption) | Basic , medium ,expert programs example in c,java,c/++

Switching Power Supply Two Outputs 25W 24V 1A 5V 1A Power Adapter AC Input 90V 264V Lighting Transformer LED Driver RSA 25D C|Switching Power Supply| - AliExpress
GitHub - navin13692/RSA-1024bit-in-C-: Simple RSA 1024bit library to encrypt and decrypt data using private public key. Best part of it, it does not have any dependancies otherthen basic standard libraries that Embedded

The C. elegans RSA Complex Localizes Protein Phosphatase 2A to Centrosomes and Regulates Mitotic Spindle Assembly: Cell




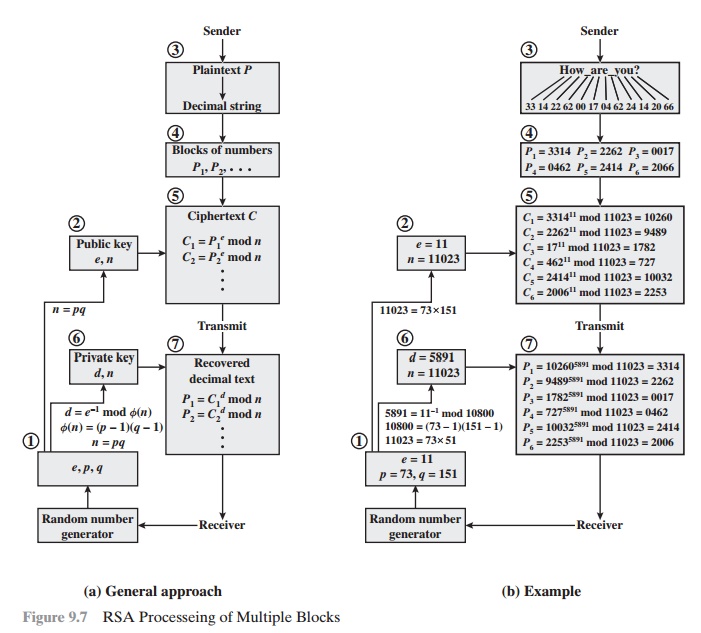





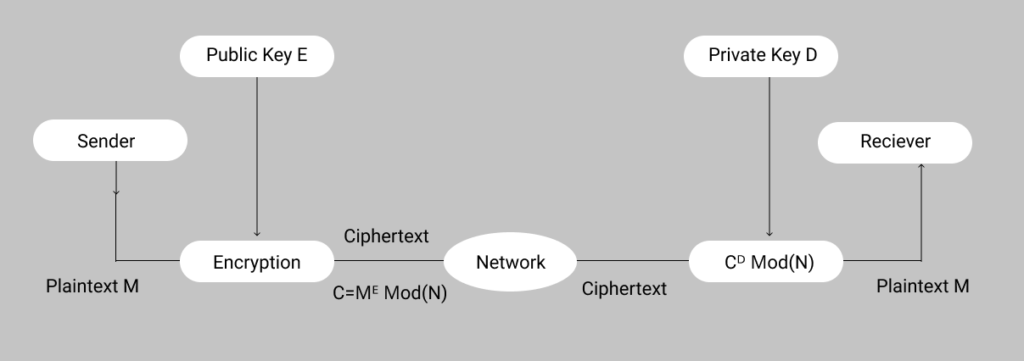




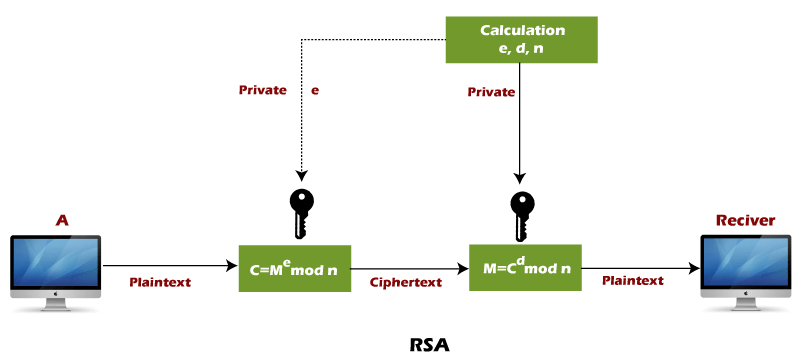



%20implementation%20in%20C.png)
